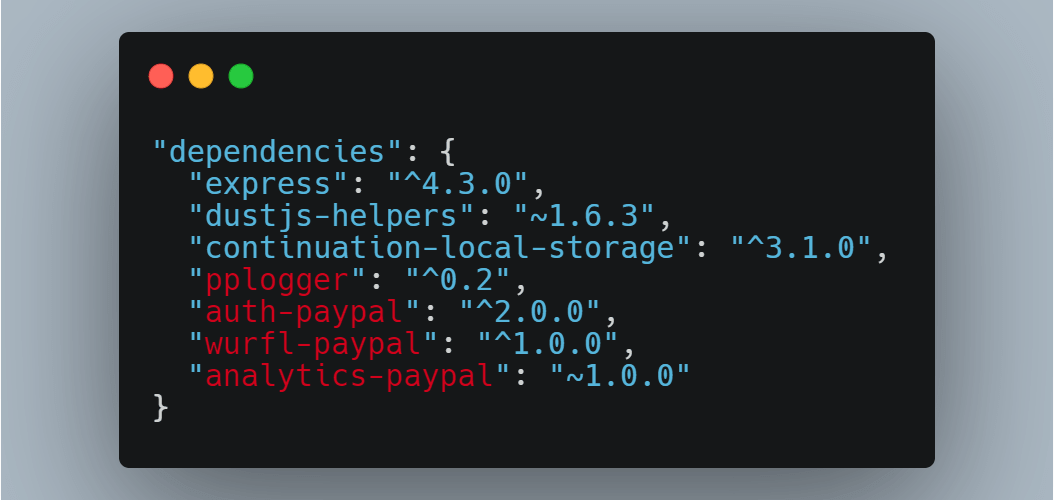
While looking at a package.json from a public project from PayPal, Alex Birsan noticed that it held some references to private NPM packages used internally by PayPal. Birsan noticed some of the manifest file packages were not present on the public npm repository but were instead PayPal’s privately created npm packages, used and stored internally …