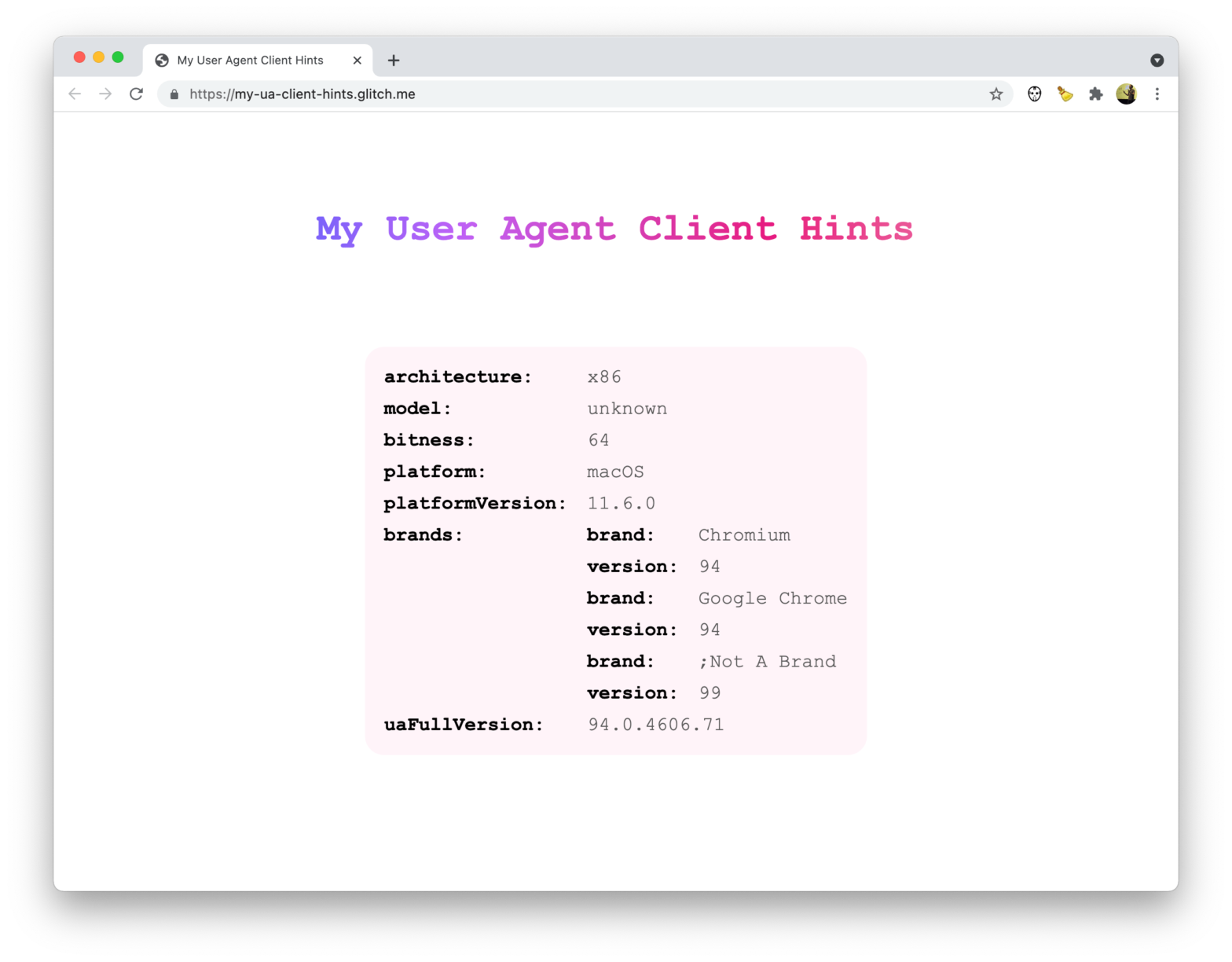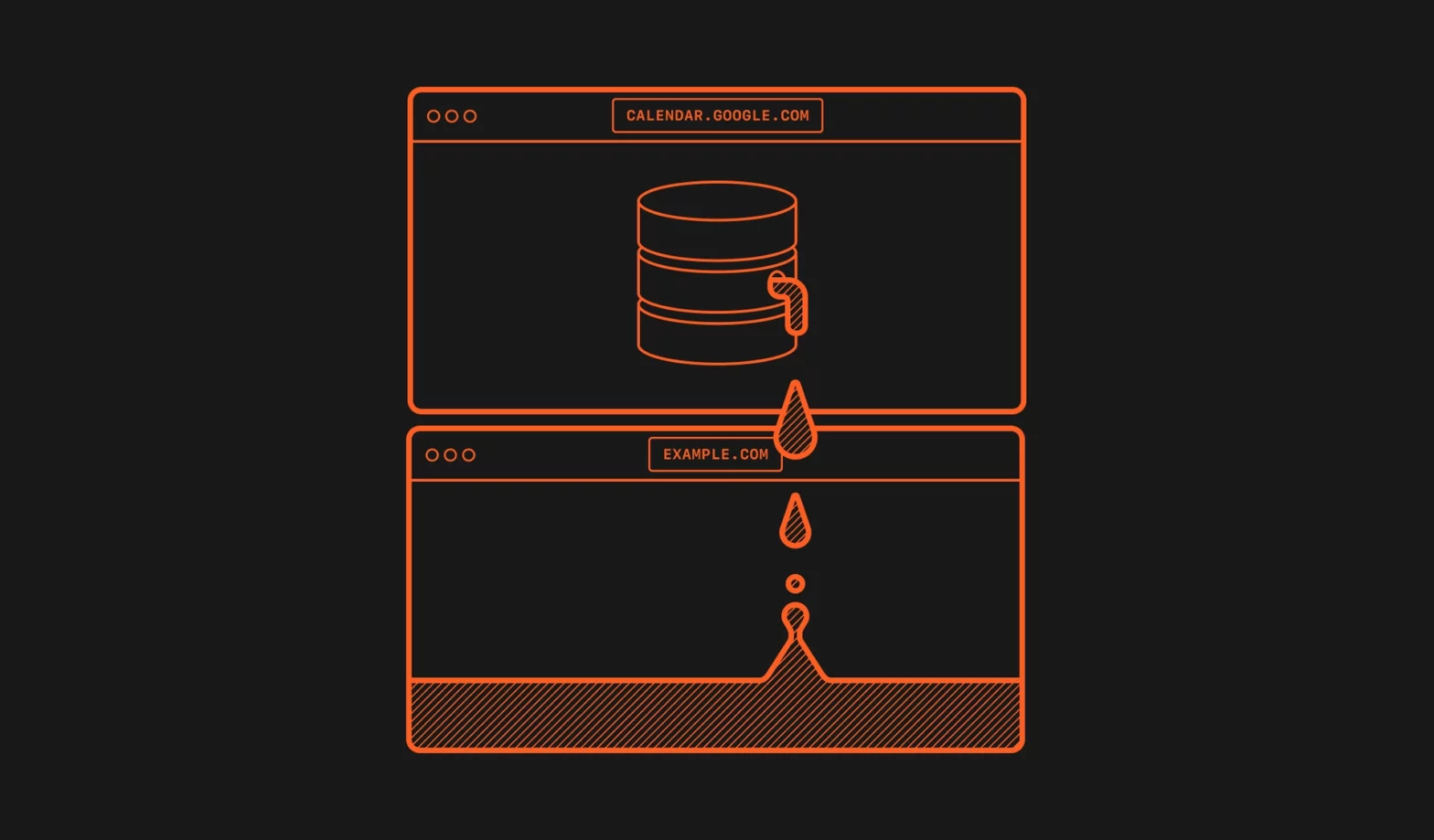
There’s a pretty nasty exploit in Safari 15, where sites/tabs that interact with an IndexedDB database leak that name to other tabs. In Safari 15 on macOS, and in all browsers on iOS and iPadOS 15, the IndexedDB API is violating the same-origin policy. Every time a website interacts with a database, a new (empty) …
Continue reading “Exploiting IndexedDB API information leaks in Safari 15”