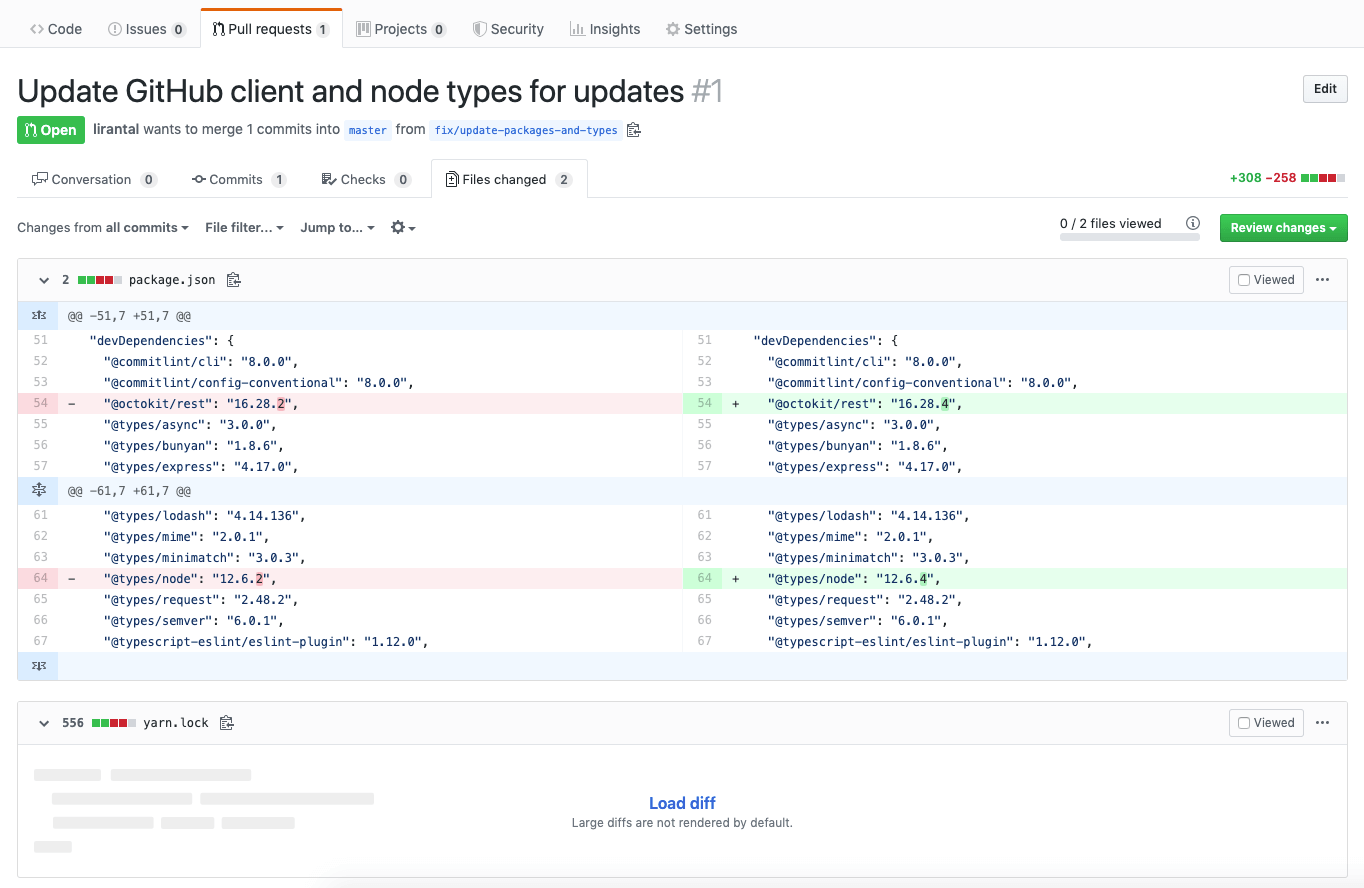
When watching a diff that contains a lockfile (say: a yarn.lock for example) on GitHub, GitHub doesn’t always show the differences (see screenshot above) as the changes in such files tend to be quite big. And even if it were to show the changes, does one really take a close look into it? With this in mind, Liran Tal started playing around to create a vector of attack using those lock files.
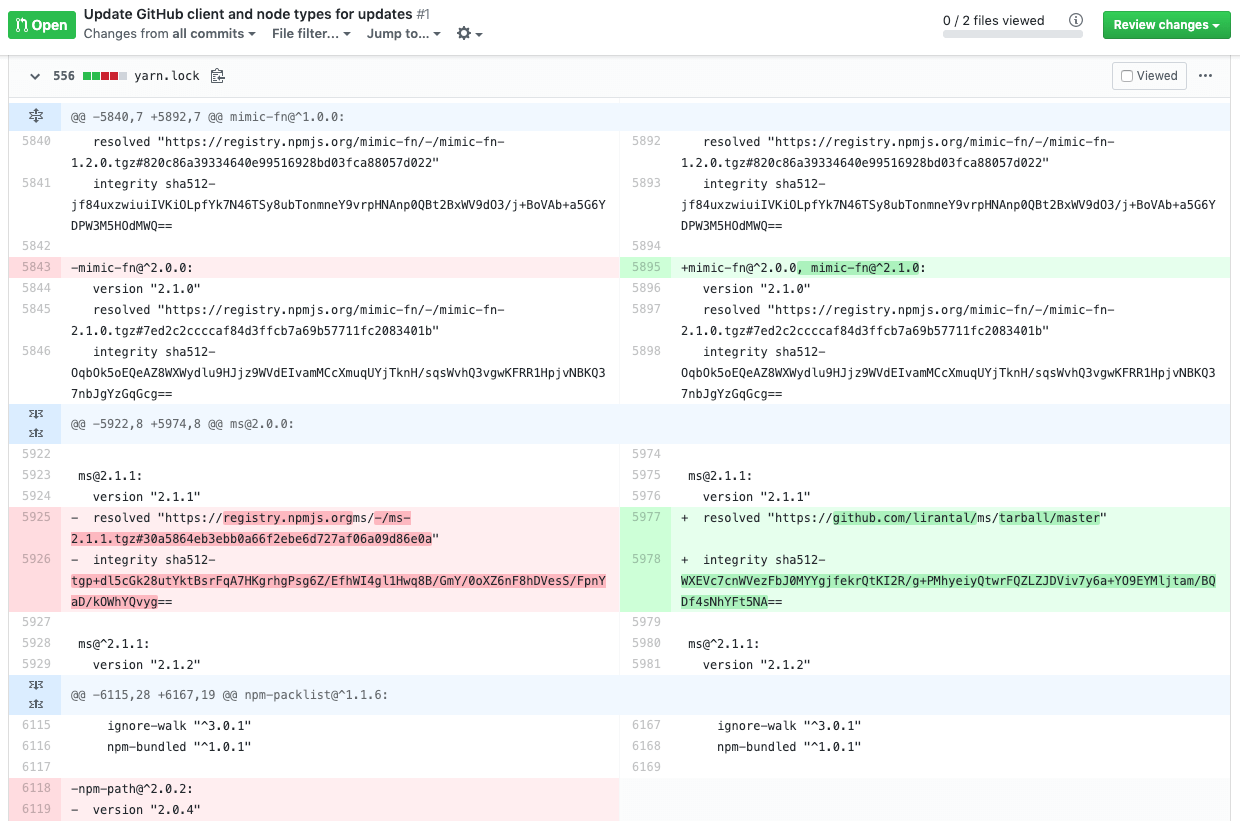
Take this diff for example:
What becomes clear when you look closer, is that I replaced the original
msnpm package to resolve it with my own version, which is stored in my GitHub repository. I should have gotten it from the official npm registry, just as was originally set in the lockfile of the project.When this pull request gets merged, I inject my malicious version of
ms@2.1.1into the code in order to control its behavior during runtime.In this way, I could introduce a backdoor, alter the logic of the ms module or I could run some postinstall scripts.
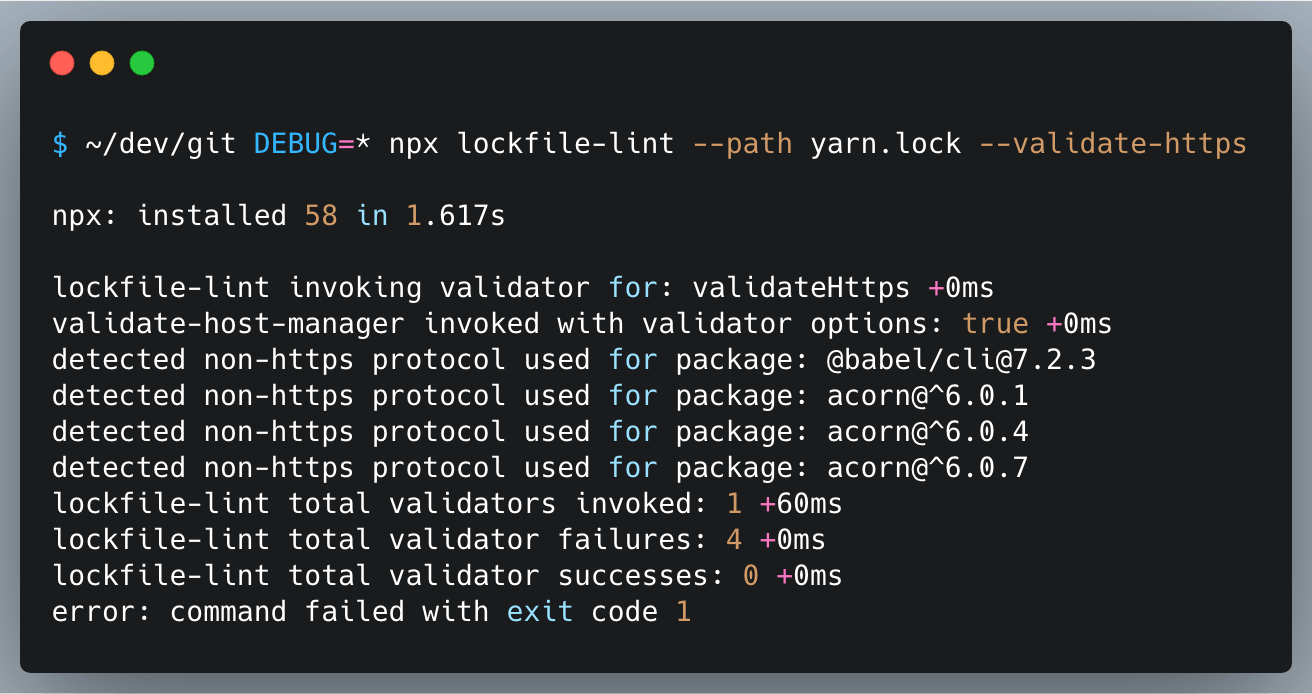
To prevent such commits from being merged, you can resort to lockfile-lint which will warn you for such issues.
As an end-user it’s wise to run npm install with --ignore-scripts.
Why npm lockfiles can be a security blindspot for injecting malicious modules →