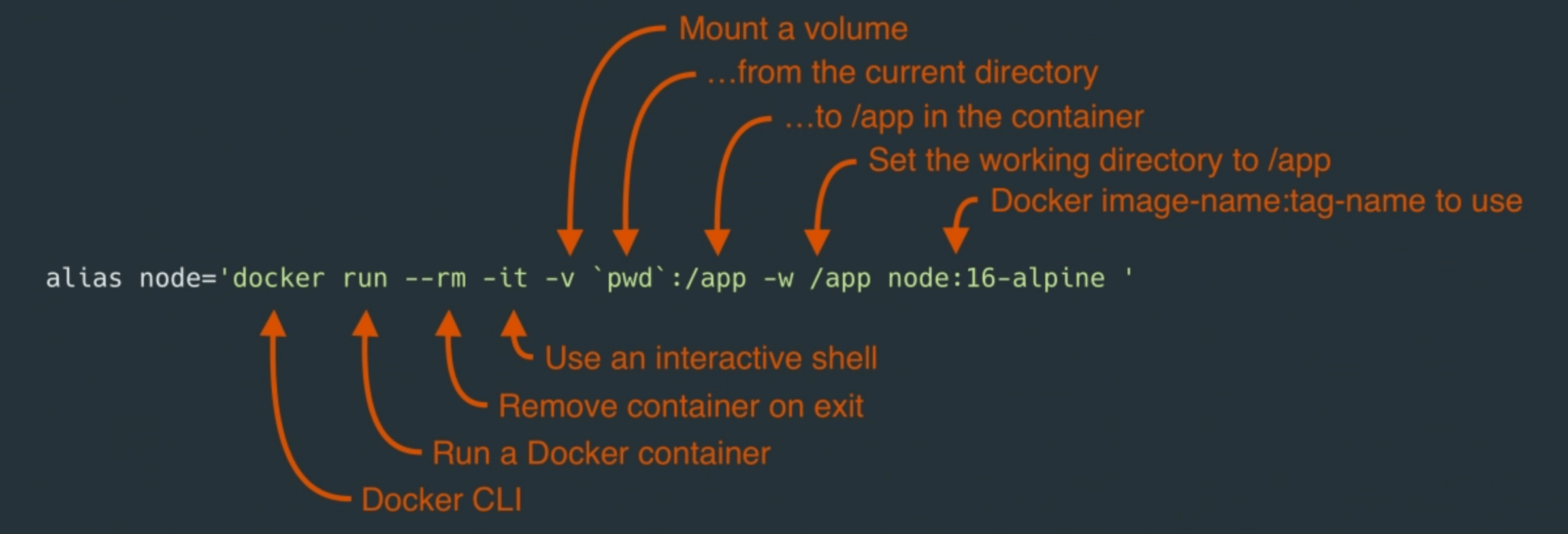
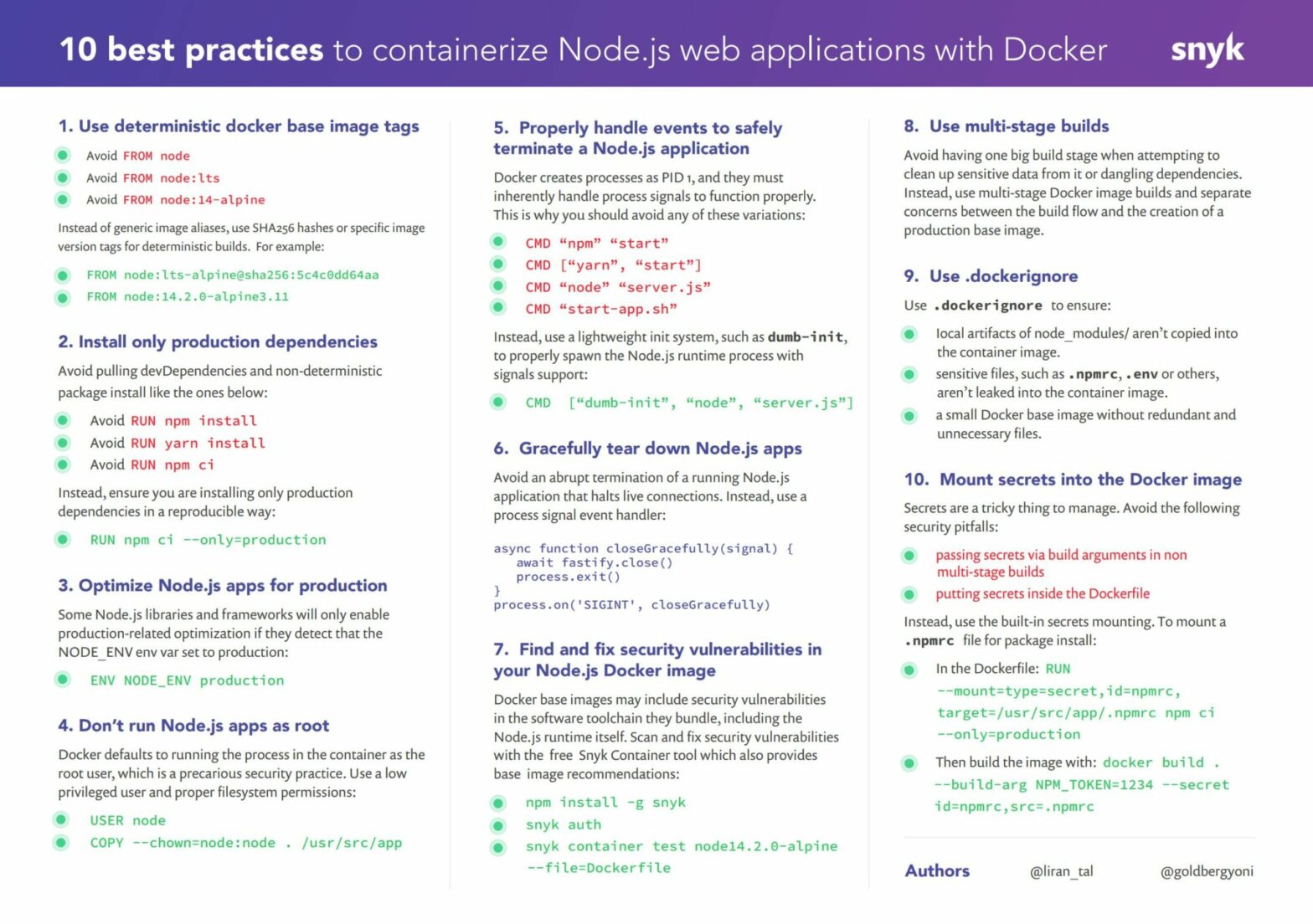
Nixery is a Docker-compatible container registry that is capable of transparently building and serving container images using Nix. Images are built on-demand based on the image name. For example: docker pull http://nixery.dev/shell/git/htop The command above will give you an image with an interactive Shell, that also has git and htop installed. Keep adding more path …