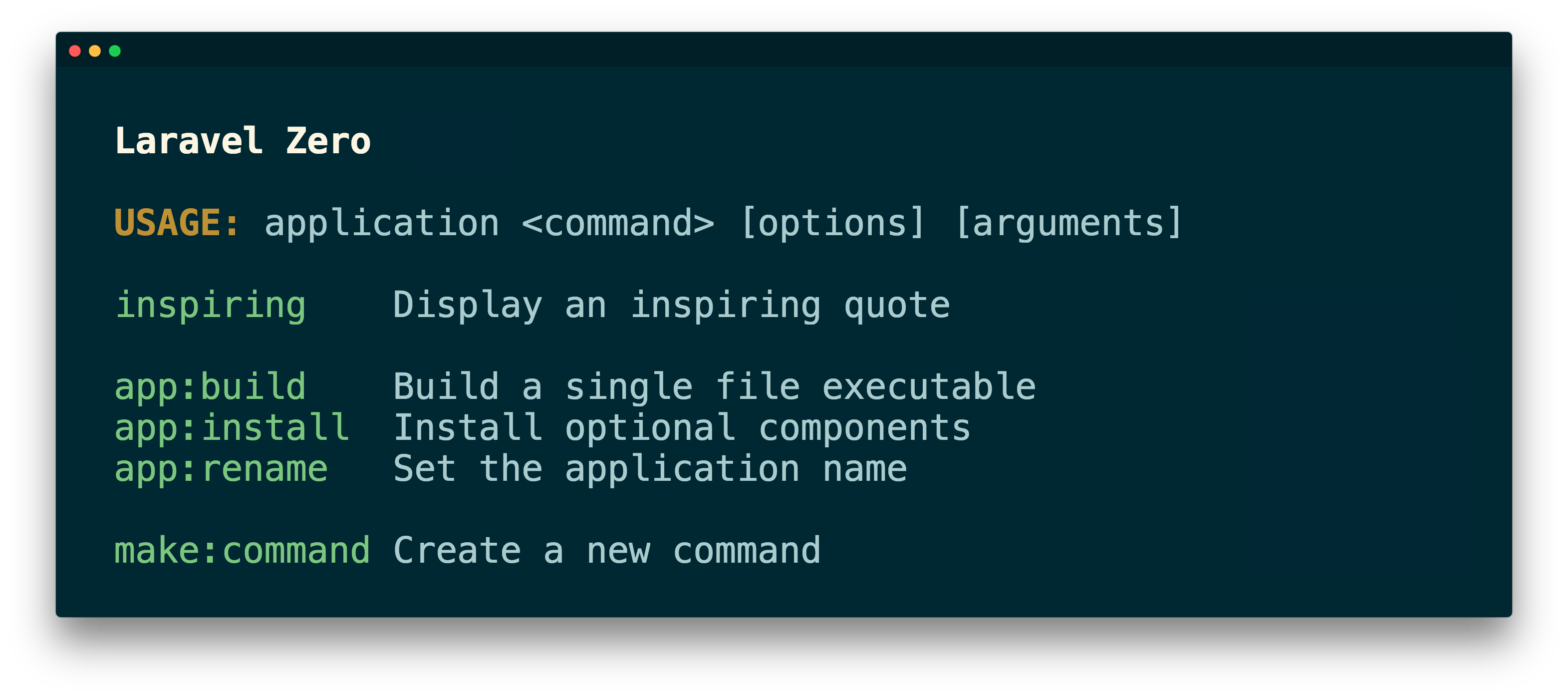
For my local PHP Development needs I use Laravel Valet. It’s easy to set up, provides HTTPS, and just works. The only downside of using it, is the fact that the selected PHP version is system-wide: switching PHP versions — using valet use php@7.4 for example — affects all sites. With the 3.0 release of …
Continue reading “Valet 3.0: Multiple/Parallel PHP Version Support”