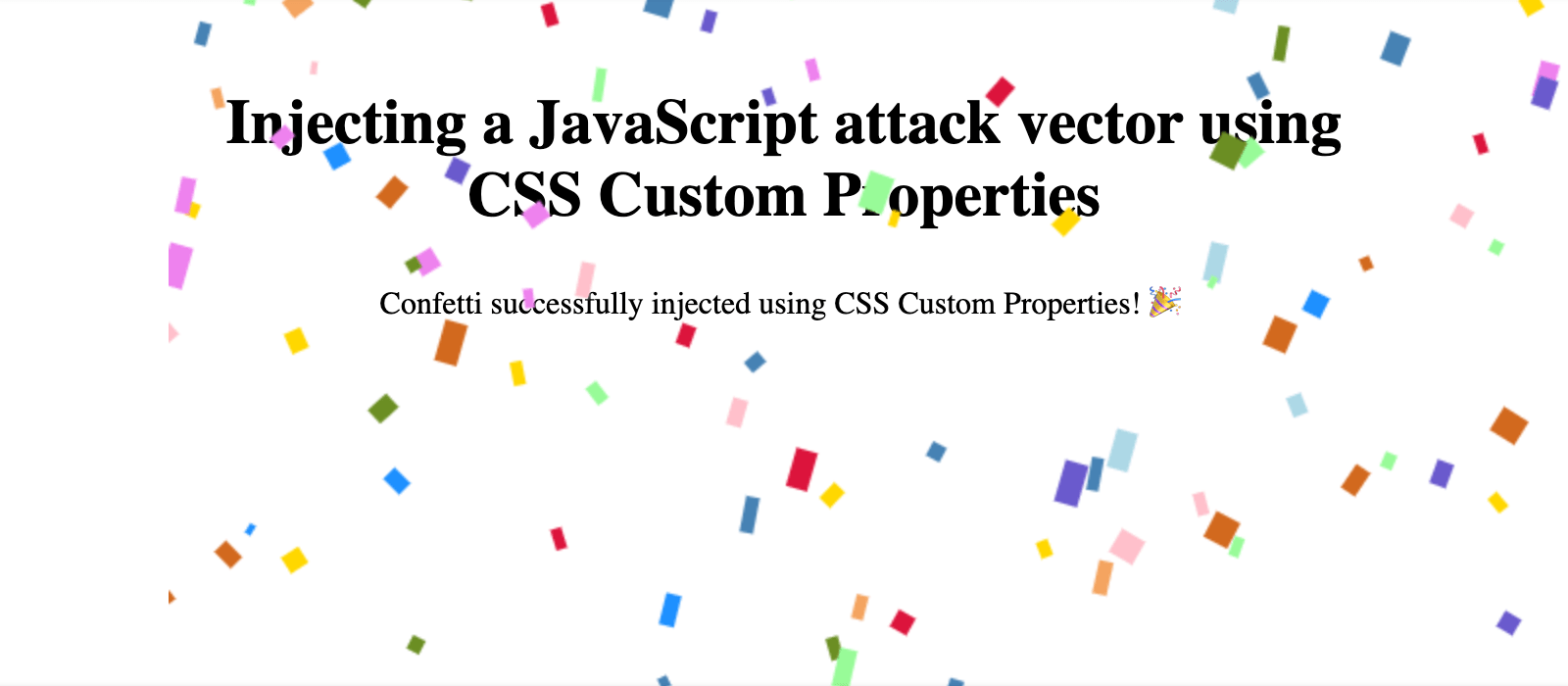
As the syntax for CSS Custom Properties is overly permissive it’s possible to store a JavaScript attack vector in them …
A rather geeky/technical weblog, est. 2001, by Bramus
laravel-cspSpeaking of Content Security Policy, the folks at Spatie – who else? – have created a Laravel Package to easily take care or your CSP needs in a Laravel-based app. Even without knowing the inner workings of the packge, the custom Policy below is easy to understand: namespace App\Services\Csp; use Spatie\Csp\Directive; use Spatie\Csp\Policies\Policy as BasePolicy; …
Continue reading “Easily set Content Security Policy headers in Laravel with laravel-csp“
An extra measure to preventing Cross-Site Scripting has now become a standard ready to be implemented. It’s as easy as including a Content-Security-Policy header on your sites Content-Security-Policy: script-src ‘self’; img-src ‘none’ With the (example) policy above, external scripts and images won’t be loaded on your site. This new header however doesn’t mean you’re fully …
Continue reading “Content Security Policy — Preventing XSS Attacks Client-side”