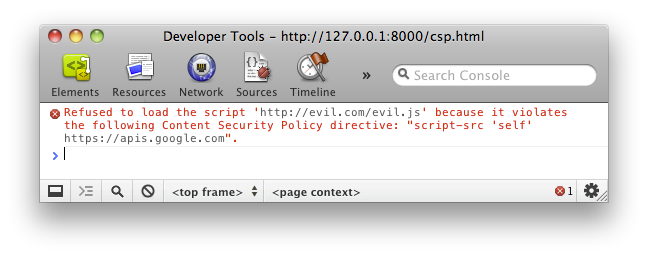
An extra measure to preventing Cross-Site Scripting has now become a standard ready to be implemented. It’s as easy as including a Content-Security-Policy header on your sites
Content-Security-Policy: script-src 'self'; img-src 'none'With the (example) policy above, external scripts and images won’t be loaded on your site. This new header however doesn’t mean you’re fully protected once you include it; you’ll still want to encode your strings serverside, as you don’t want *any* HTML tags to be injected. Also, older browsers still will be a target as they don’t understand the header (but that on the other hand could be a huge argument to pushing clients towards the newest version of their browser).
Alternatively you can also use a meta tag.
More on Content Security Policy: An Introduction To Content Security Policy →
Leave a comment