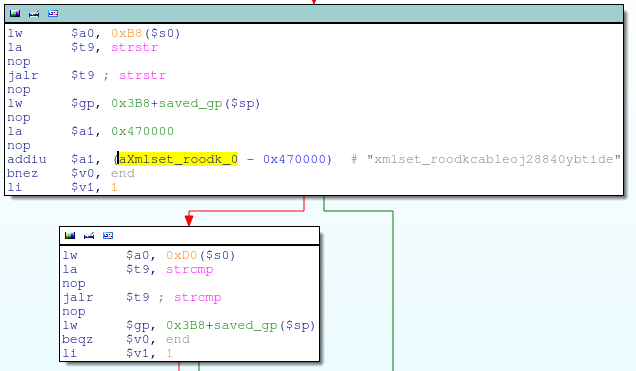
alpha_auth_checkitself is a fairly simple function. It does a fewstrstr’s andstrcmp’s against some pointers in thehttp_request_tstructure, then callscheck_login, which actually does the authentication check. It is the finalstrcmphowever, which proves to be the most compelling: This is performing astrcmpbetween the string pointer at offset0xD0inside thehttp_request_tstructure and the string “xmlset_roodkcableoj28840ybtide”; if the strings match, thecheck_loginfunction call is skipped andalpha_auth_checkreturns1(authentication OK).
“xmlset_roodkcableoj28840ybtide” is “edit by 04882 joel backdoor” spelled backwards. Some guy, that Joel. 🙂